
Love AnyBackup all-in-one backup machine
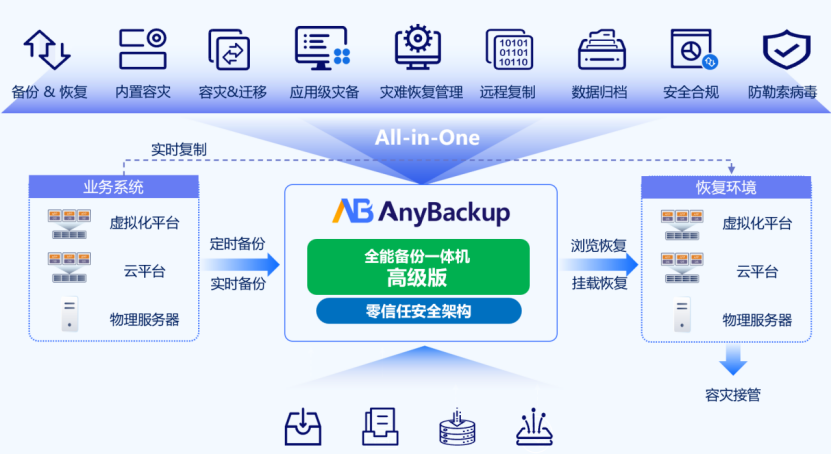
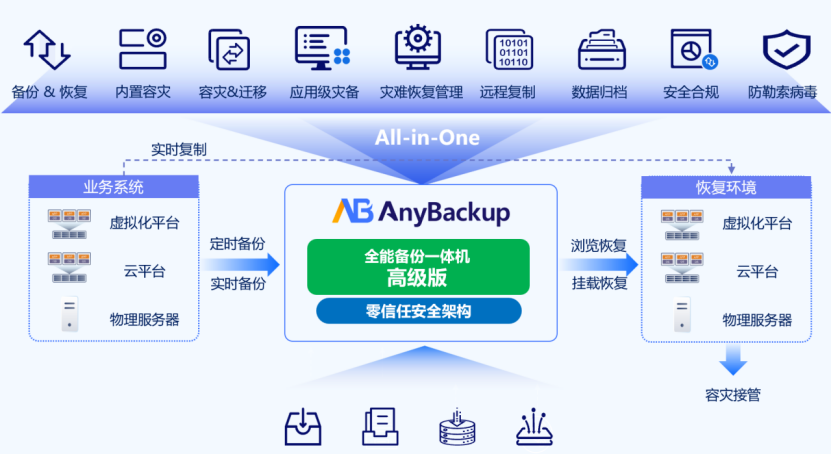
AnyBackup All-in-One Backup Advanced Edition is based on the x86 hardware architecture, supports single-machine deployment and cluster deployment, uses a distributed architecture (multiple storage services, clusters), and has distributed storage capabilities (EC/ triple copy). The system provides comprehensive data protection solutions including scheduled backups, real-time backup, and instant replication. It supports advanced capabilities such as UNIX backup and unified operational management, along with built-in disaster recovery features like disaster migration. Through a zero-trust security architecture, it effectively guards against ransomware threats, enabling minute-level mount restoration and takeover to significantly enhance disaster recovery efficiency.
Category:
Keywords:
Tel
Product Details
AnyBackup All-in-One backup machine is designed for small and medium enterprises. The main features are:
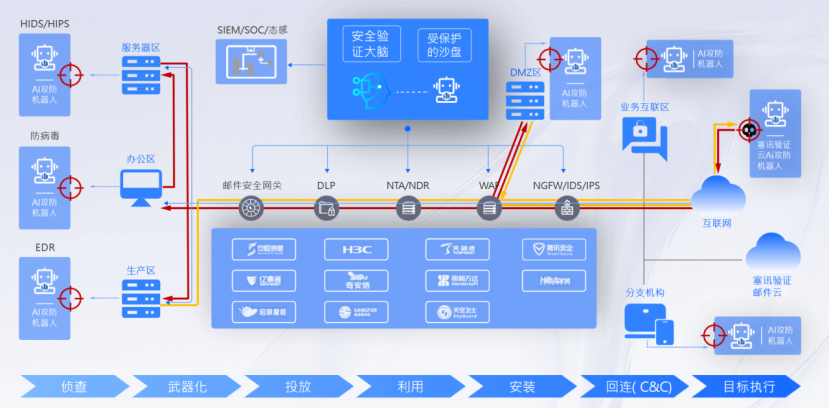
- Comprehensive protection, compatible with 1700 + applications, support for all kinds of data backup, disaster recovery and migration, adapt to multiple scenarios.
- Safe and reliable, using zero trust architecture, with multiple protection such as data immutability, isolation and recovery.
- Experience high efficiency, resource perspective management reduces 90% of the workload, support minute-level recovery, backup efficiency and low cost.
- Economical, practical, cost control, flexible expansion, meet the needs of hierarchical protection, anti-ransomware and other needs.
Architecture description

AnyBackup All-in-One Backup Advanced Edition is based on the x86 hardware architecture, supports single-machine deployment and cluster deployment, uses a distributed architecture (multiple storage services, clusters), and has distributed storage capabilities (EC/ triple copy).
The system provides comprehensive data protection solutions including scheduled backups, real-time backup, and instant replication. It supports advanced capabilities such as UNIX backup and unified operational management, along with built-in disaster recovery features like disaster migration. Through a zero-trust security architecture, it effectively guards against ransomware threats, enabling minute-level mount restoration and takeover to significantly enhance disaster recovery efficiency.
product superiority
1. Comprehensive data protection capability, covering multiple scenarios
- Extensive compatibility: supports more than 1700 applications, covering mainstream and domestic databases (Oracle, MySQL, OpenGauss, etc.), virtualization platforms (VMware, Hyper-V, etc.), cloud platforms (Aliyun, Huawei Cloud, etc.) and operating systems (Windows, Linux, etc.), taking into account current and future needs.
- Full-process protection: Provides scheduled backup, real-time backup, mount recovery, disaster recovery migration and other capabilities, which are suitable for structured and unstructured data to meet the RTO (recovery time goal) and RPO (recovery point goal) requirements of different services.
- Multi-cloud and heterogeneous support: enables cross-cloud and cross-platform data flow and recovery, supports virtual machine heterogeneous recovery and database heterogeneous migration, and solves the protection problem under massive data and complex architecture.
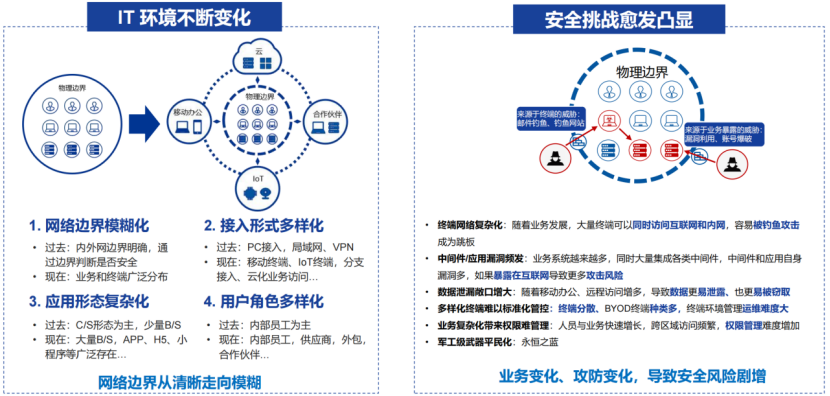
2. Zero-trust security architecture to resist risks in an all-round way
- Data is not tampered with: The immutable storage technology is adopted, combined with mandatory data retention and built-in clock to prevent ransomware tampering and internal malicious operation. The kernel-level technology has no performance loss.
- Isolation and protection: Build an isolation and recovery environment based on Air-Gap, without open ports, and cooperate with virus scanning and killing drills to ensure that backup data can be safely recovered.
- Full-link encryption: Data transmission and storage encryption is realized through AES256, SM4 and other algorithms. Three-layer key system + two-factor authentication ensures zero data leakage.
- Compliance and verification: Support automatic data consistency verification and fine control of permissions (RBAC) to meet compliance requirements such as ETC 2.0 and Data Security Law.
3. extreme efficiency and experience, greatly reduce management costs
- Efficient backup and recovery: No synthetic permanent incremental backup time is reduced by 72.3%, the backup window is shortened, the mount time is reduced to minutes (17.57TiB data takes only 2 minutes and 22 seconds), and the disaster recovery efficiency is increased by 13 times.
- Lightweight management: The resource perspective management mode reduces the workload by 90% (the annual management of 2000 virtual machines is reduced from 62.5 people/day to 6.25 people/day), and supports global performance monitoring and one-click operation
- Cost optimization: The fifth-generation deduplication technology reduces storage costs by 70%, and the standard edition integrates backup and archiving, reducing overall costs by 50%; it supports Scale out expansion, and the average cost is lower in massive data scenarios.
4. flexible adaptation and high cost performance to meet the needs of small and medium-sized enterprises
- Version subdivision: The basic version meets the basic needs of small and micro customers, the standard version balances comprehensiveness and economy, and the advanced version provides extreme security and efficiency, covering 10TB-200TB data scale.
- Scenario adaptation: Supports scenarios such as hierarchical data protection, remote disaster recovery, anti-ransomware, and compliant archiving. Seamless connection between local and remote disaster recovery ensures business continuity.
Certificate of Honor