
Aishu AnyBackup All-in-One Backup Appliance
AnyBackup all-round backup appliance is designed for small and medium-sized enterprises. The main features are: ● Comprehensive protection, compatible with 1700 + applications, supports various data backup, disaster recovery migration, etc., and is suitable for multiple scenarios. ● Safe and reliable, adopts a zero-trust architecture, and has multiple protections such as data immutability and isolated recovery. ● Efficient experience, resource perspective management reduces workload by 90%, supports minute-level recovery, high backup efficiency, and low cost. ● Economical and practical, cost-controllable, flexible expansion, to meet various needs such as hierarchical protection and anti-ransomware.
Category:
Keywords:
Tel
Product Details
AnyBackup all-in-one backup appliance is designed for small and medium-sized enterprises, with the following main features:
● Comprehensive protection, compatible with 1700+ applications, supports various data backup, disaster recovery migration, etc., suitable for multiple scenarios.
● Safe and reliable, adopts a zero-trust architecture, and has multiple protections such as data immutability and isolated recovery.
● Efficient experience, resource perspective management reduces workload by 90%, supports minute-level recovery, high backup efficiency, and low cost.
● Economical and practical, cost-controllable, flexible expansion, to meet various needs such as hierarchical protection and anti-ransomware.
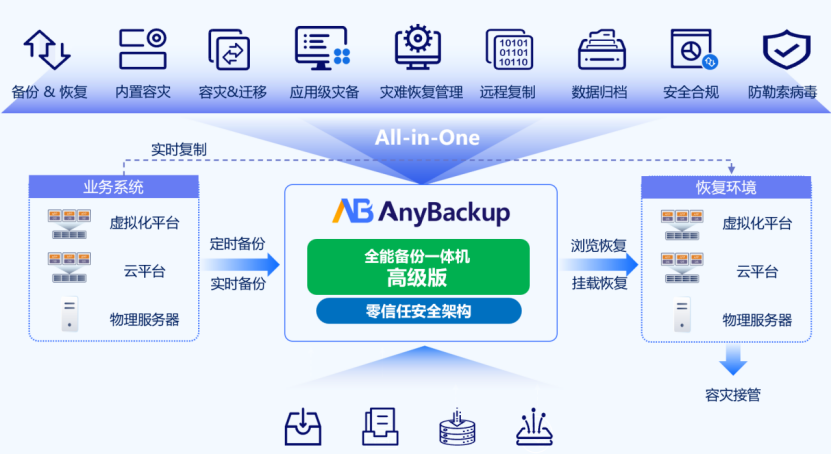
Architecture description

AnyBackup all-in-one backup appliance advanced edition is based on x86 hardware architecture, supports stand-alone deployment and cluster deployment, and adopts a distributed architecture (multi-storage service, cluster), with distributed storage capabilities (EC / three copies).
In terms of functions, it covers data protection methods such as scheduled backup, real-time backup, and real-time replication, supports advanced capabilities such as UNIX backup and unified operation management, and also has disaster recovery migration and built-in disaster recovery functions. It can comprehensively resist ransomware viruses through a zero-trust security architecture, realize minute-level mount recovery and takeover, and improve disaster recovery efficiency.
Product advantages
I. Comprehensive data protection capabilities, covering diverse scenarios
● Widely compatible: Supports 1700+ applications, covering mainstream and localized databases (Oracle, MySQL, OpenGauss, etc.), virtualization platforms (VMware, Hyper-V, etc.), cloud platforms (Alibaba Cloud, Huawei Cloud, etc.) and operating systems (Windows, Linux, etc.), taking into account current and future needs.
● Full-process protection: Provides capabilities such as scheduled backup, real-time backup, mount recovery, and disaster recovery migration, adapts to structured and unstructured data, and meets the RTO (Recovery Time Objective) and RPO (Recovery Point Objective) requirements of different businesses.
● Multi-cloud and heterogeneous support: Realizes cross-cloud and cross-platform data flow and recovery, supports heterogeneous virtual machine recovery and heterogeneous database migration, and solves the protection problems under massive data and complex architecture.
II. Zero-trust security architecture to comprehensively resist risks
● Data cannot be tampered with: Adopts immutable storage technology, combined with mandatory data retention and built-in clock, to prevent ransomware viruses from tampering and internal malicious operations. The kernel-level technology has no performance loss.
● Isolation and protection: Build an isolated recovery environment based on Air-Gap, with no port open, and cooperate with virus detection and killing drills to ensure that backup data can be safely recovered.
● Full-link encryption: Data transmission and storage encryption are realized through algorithms such as AES256 and SM4, three-layer key system + two-factor authentication to ensure zero data leakage.
● Compliance and verification: Supports automatic data consistency verification and fine-grained permission control (RBAC) to meet the compliance requirements of Information Security Level Protection 2.0 and Data Security Law.
III. Ultimate efficiency and experience, greatly reducing management costs
● Efficient backup and recovery: Non-synthetic permanent incremental backup shortens the backup window by 72.3%, minute-level mount recovery (17.57TiB data only takes 2 minutes and 22 seconds), and disaster recovery efficiency is increased by 13 times.
● Lightweight management: Resource perspective management mode reduces workload by 90% (annual management volume of 2000 virtual machines drops from 62.5 people/day to 6.25 people/day), supports global performance monitoring and one-click operation
● Cost optimization: The fifth-generation data deduplication technology reduces storage costs by 70%, the standard version integrates backup and archiving, and the comprehensive cost is reduced by 50%; it supports Scale out expansion, and the average cost is lower in massive data scenarios.
IV. Flexible adaptation and high cost performance to meet the needs of small and medium-sized enterprises
● Version segmentation: The basic version meets the basic needs of small and micro customers, the standard version balances comprehensiveness and economy, and the advanced version provides ultimate security and efficiency, covering a data scale of 10TB-200TB.
● Scenario adaptation: Supports hierarchical data protection, off-site disaster recovery, anti-ransomware, compliance archiving and other scenarios, and seamlessly connects local and off-site disaster recovery to ensure business continuity.
Certificate of Honor