
Breach and Attack Simulation BAS
Enterprises have already purchased and deployed a large number of security protection devices, so is the enterprise's security defense system strong enough? The essence of cybersecurity is confrontation. In traditional security construction, the defender's perspective is to design measurement indicators around the product capabilities of various security-related aspects, so as to ensure that all capabilities related to security products are fully utilized; while the attacker's perspective is to use intruder tactics, techniques, and processes to discover potential risks.
Category:
Keywords:
Tel
Product Details
Now that the company has purchased and deployed a large number of security protection devices, is the company's security defense system strong enough?
The essence of cybersecurity is confrontation. In traditional security construction, the defender's perspective is to design measurement indicators around various security-related product capabilities to ensure that all security product-related capabilities are fully utilized; while the attacker's perspective is to use intruder tactics, techniques, and processes to discover potential risks.
With the trend of actual combat offensive and defensive and the drive of various policies, enterprise network security concepts and defense strategies have shifted from passive defense to active defense. In order to better cope with the actual combat network security environment, continuous challenges and verification of the current network security construction are carried out to identify security weaknesses, improve the response capabilities of the security team, and enhance the overall security defense capabilities of the enterprise. The industry has proposed a more realistic, dynamic, and practical security assessment and training method: intrusion and attack simulation. 
Product value:
● Simulate thousands of valuable attack behaviors
By collecting the latest and most classic APT attack methods, our customers can use these real attack scenarios to verify the effectiveness of the defense system. These attack methods cover multiple attack dimensions such as network, endpoint, email, and industry. Spanning different stages of the attack chain, corresponding to multiple behavior types such as authentication, C&C, data leakage, DoS, malicious file transfer, MITM, remote access, defense evasion, reconnaissance, and Web vulnerability exploitation. Each attack action will have a very detailed description. At the same time, users can also customize new attack behaviors.
● Quickly verify the defense capabilities against new attacks
When new attacks and 0-days are exposed, many users' patches cannot be fixed immediately. Various security vendors generally launch corresponding protection signature (virtual patch) updates to help users protect against new attacks. However, from the user's perspective, after updating the virtual patch, it is impossible to quickly verify the effectiveness of the virtual patch when facing real attacks.
● Environmental Change Detection
The IT scale of enterprises is huge, and changes in security protection capabilities in the environment are often not perceived by the security team in the first time. The platform can continuously monitor changes in protection capabilities in the IT environment, and can set up to simulate specific attacks weekly, daily, and hourly.
When a change in protection capability is detected, the security operations team is proactively notified.
● Attack and Defense Drill
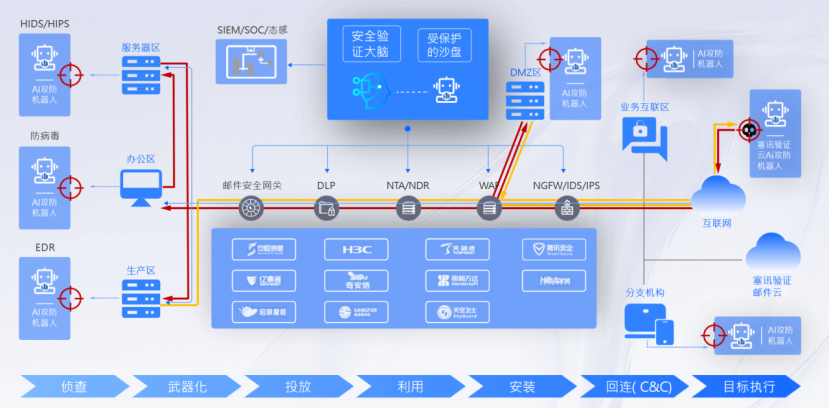
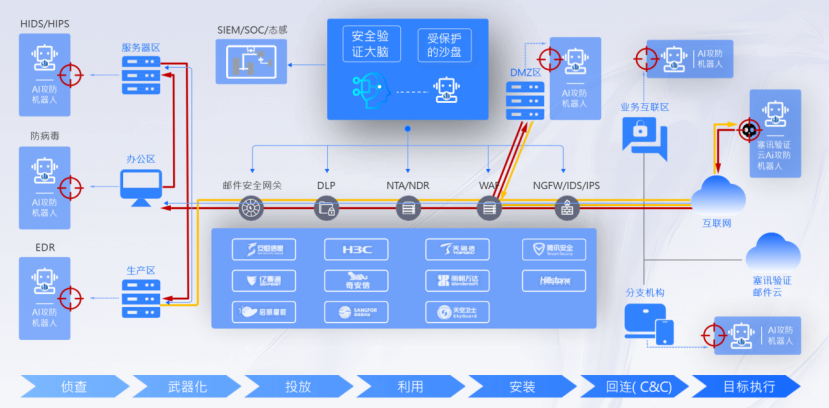
Simulate attack tests on the target in a fine-grained manner according to the KillChain model, presenting the complete attack chain and attack methods, exposing weaknesses without affecting business continuity.
● Security Verification
Not only provides effectiveness verification for single control measures such as firewalls, WAFs, and EDRs, but also provides scenario-based security verification capabilities for ransomware defense, APT detection, and cloud security compliance.
● Security Assessment
Through continuous verification, effectively quantify and assess enterprise security risks, manage enterprise network security posture, and balance the relationship between security and business when facing threat changes and business drivers. Based on practical experience, infer the possibility and effectiveness of real-world confrontation from the perspective of facts and data.
● Budget Management
Under the general background of reducing costs and increasing efficiency, enterprise security construction often carries out strict cost control in terms of budget. We hope to use effective verification methods to ensure that appropriate budgets are invested in appropriate places to make capital utilization higher.
Certificate of Honor