
Zero Trust
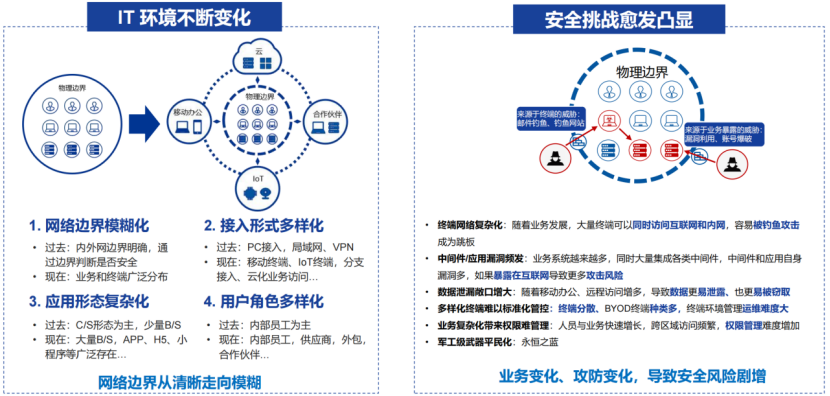
As the digital transformation continues to accelerate, emerging technologies and innovative businesses are constantly breaking the original security boundaries of enterprises, and the traditional boundary-based security model has become history. Today's workplace has expanded to any location, any time, and any device. Traditional decentralized security solutions have vulnerabilities, providing opportunities for attackers. Unlike traditional security models that rely on security boundaries to defend against threats, adopting the right zero-trust strategy can help your organization move from a static, network-based defense model to one that focuses on users, assets, and resources. The zero-trust security model follows three principles: explicitly verify, use least privilege access, and assume breach.
Category:
Keywords:
Tel
Product Details
As the digital transformation continues to accelerate, emerging technologies and innovative businesses continue to break the original security boundaries of enterprises, and the traditional boundary-based security model has become history. Today's workplace has expanded to any location, any time, and any device. Traditional decentralized security solutions have vulnerabilities, providing opportunities for attackers. Unlike traditional security models that rely on security boundaries to defend against threats, adopting the right zero-trust strategy can help your organization shift from a static, network-based defense model to one that focuses on users, assets, and resources. The zero-trust security model follows three principles: explicitly verify, use least privilege access, and assume breach.

Product value:
● Build borderless access control capabilities
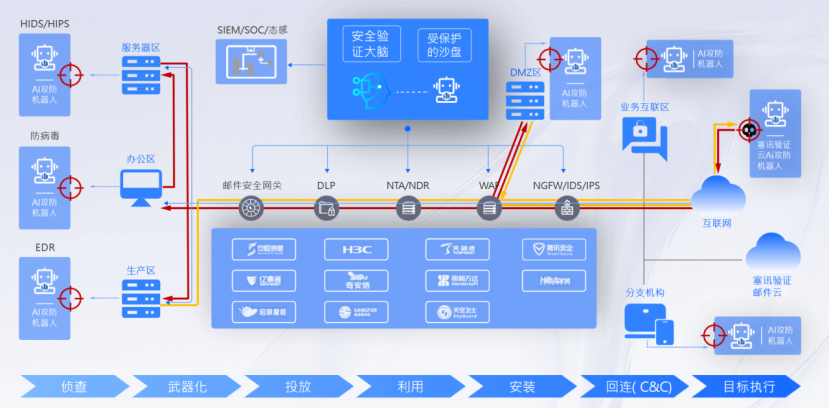
Under the zero-trust architecture, based on digital identity, realize the trusted identification of users, and complete identity authentication and single sign-on. Through network invisibility, continuous verification, fine-grained dynamic access control and other functions, it can effectively converge the network exposure surface, reduce the chance of vulnerabilities being exploited, and prevent potential attacks.
● Build continuous trust assessment capabilities
Under the zero-trust architecture, through continuous trust assessment of the access subject, the access subject's access rights are dynamically adjusted and the access identity authentication is dynamically adjusted. When the security baseline is not met or the system is running with problems, access is blocked and login is logged out in time to ensure that only secure and compliant terminals can access business resources, and to prevent the use of vulnerable or compromised terminals as stepping stones to attack business resources.
● Build emergency response capabilities
The effectiveness of traditional boundary security is declining, and constantly evolving network threats and high-value data drivers pose higher challenges to secure access, access control, and data leakage protection. Through linkage with security emergency response, an integrated active security defense system based on zero trust is built for enterprises, thereby maximizing security protection effectiveness.
● Build security visualization capabilities
Through visualization technology, the access path, access traffic, and abnormal user access behavior are visually displayed. The online device status, statistics, policy execution status, execution path, etc. can also be visualized, helping security operation personnel to more intuitively and comprehensively understand the security status and behavior of the access subject, so as to find risk points more quickly and accurately, trigger security responses, and support security decisions.
● Build data protection and governance
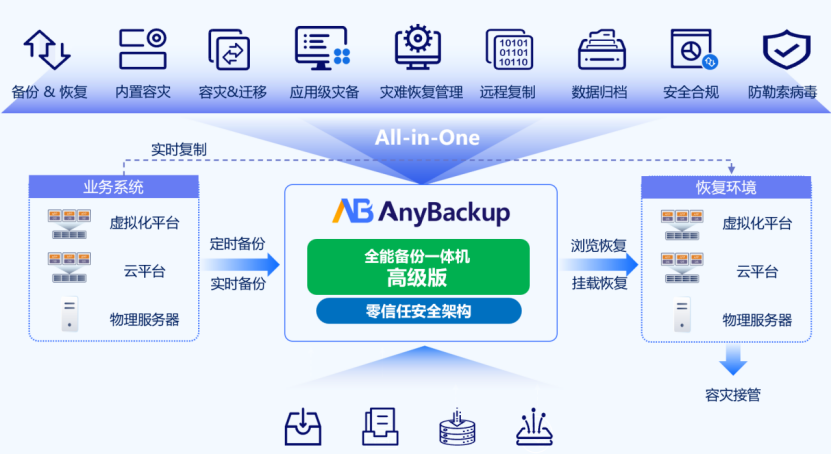
Zero-trust data protection and governance methods help maximize the commercial value of data while minimizing security and compliance risks. It protects data and user identities by implementing strict management practices, enabling employees to securely share information with partners, vendors, and customers.
● Proactively meet legal and regulatory requirements
Implementing a comprehensive zero-trust architecture helps proactively meet regulatory and compliance requirements, discover and achieve end-to-end visibility of critical assets, and protect and manage an organization's entire data assets through unified data governance and risk management. Even better, zero-trust strategies often go beyond the requirements of other regulations and can meet new regulatory requirements with fewer overall system changes, enabling your business to grow in a flexible and efficient manner.
Certificate of Honor